Identity and Access Management (IAM) Tools: Features, Benefits, and Comparisons
IAM tools are critical for managing user access securely and efficiently. They help organizations enforce access policies, automate provisioning, and conduct access reviews effectively. Below is an in-depth look at the top IAM tools, their features, and how they compare.
1. Overview of IAM Tools
IAM solutions are broadly categorized into:
Identity Governance and Administration (IGA) – Manages user identities and automates access reviews.
Privileged Access Management (PAM) – Secures high-risk accounts with Just-in-Time access.
Access Management (AM) – Controls authentication and authorization, including Single Sign-On (SSO) and Multi-Factor Authentication (MFA).
User Lifecycle Management – Automates user provisioning and deprovisioning.
Federated Identity & SSO – Enables seamless login across multiple systems.
3. Detailed Features & Benefits of IAM Solutions
A. Identity Governance & Administration (IGA)
Helps organizations manage user identities, enforce least-privilege access, and conduct access reviews.
✅ Key Features:
Automated user provisioning & deprovisioning
Access certification & compliance reporting
Role-based & attribute-based access control (RBAC/ABAC)
AI-driven role mining & access recommendations
Self-service access requests & approvals
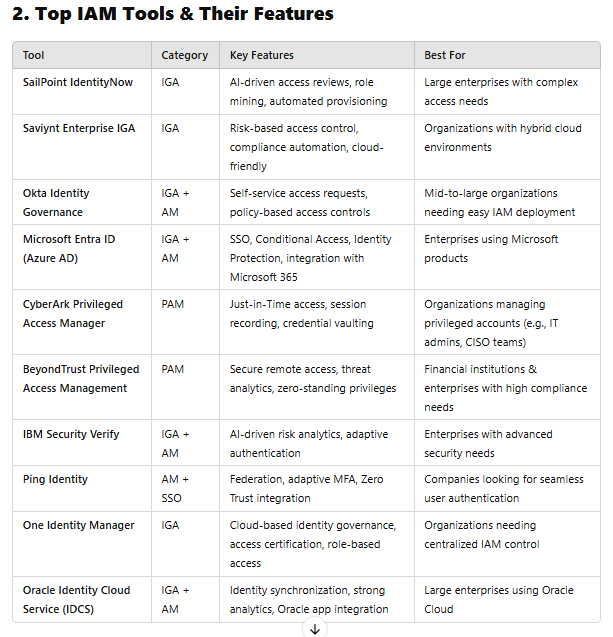
🔹 Best Tools: SailPoint, Saviynt, Okta Identity Governance, One Identity
B. Privileged Access Management (PAM)
Secures high-risk accounts by enforcing Just-in-Time (JIT) access, eliminating standing privileges, and monitoring privileged sessions.
✅ Key Features:
Secure credential storage & password vaulting
Just-in-Time (JIT) access with automatic expiration
Session recording & forensic auditing
Threat analytics for privileged accounts
Integration with SIEM & SOAR tools for real-time monitoring
🔹 Best Tools: CyberArk, BeyondTrust, Delinea (formerly Thycotic)
C. Access Management (AM)
Ensures secure authentication and authorization, reducing reliance on passwords and enabling Zero Trust security.
✅ Key Features:
Single Sign-On (SSO) & federated identity management
Multi-Factor Authentication (MFA) & passwordless authentication
Adaptive access policies based on risk signals
Integration with cloud applications (AWS, Google Cloud, Microsoft 365)
🔹 Best Tools: Microsoft Entra ID (Azure AD), Ping Identity, Okta, IBM Security Verify
D. User Lifecycle Management
Automates user onboarding, role assignments, and offboarding to prevent orphaned accounts and unauthorized access.
✅ Key Features:
Integration with HR systems (Workday, SAP, Oracle)
Automated role-based provisioning
Real-time deprovisioning for terminated users
Least-privilege enforcement across departments
🔹 Best Tools: SailPoint, One Identity, Oracle IDCS
5. Future Trends in IAM
AI & Machine Learning → Enhanced anomaly detection, risk-based access control.
Zero Trust Security → Continuous authentication & least privilege enforcement.
Passwordless Authentication → Adoption of FIDO2, biometric & adaptive authentication.
Cloud-Native IAM → Scalable solutions for multi-cloud environments.
Decentralized Identity → Blockchain-based identity verification.
Final Recommendations
For enterprises needing robust governance: SailPoint or Saviynt.
For Microsoft-centric organizations: Microsoft Entra ID.
For managing privileged access: CyberArk or BeyondTrust.
For user-friendly IAM with strong SSO/MFA: Okta or Ping Iden